Online fraud is a huge problem for companies and consumers, and it’s growing exponentially. Everything from bank accounts to loyalty programs and gift cards, even health insurance accounts are prime targets for fraudsters armed with databases of stolen credentials. And it’s not stopping there, any account that can be monetized is now on the attacker’s list.
Fraud has been a consistent problem on the internet, but as of late it’s dwarfing other types of attacks in the wild – so why the big increase in online fraud? It’s now easier than ever for cyber thieves to steal user accounts running credential stuffing attacks a.k.a. account takeovers (ATOs). ATOs are typically easier than exploiting the web app itself, they’re hard to identify, and generally carry less risk / attention if the attacker does get caught. The dark web is chock full of professionally-run sites offering botnets, password databases, human CAPTCHA solving and click farm services, all for not a lot of dinero.
If you read our ASM vs. AWAF article, you learned F5’s Advanced Web Application Firewall (dubbed “AWAF”) includes everything that F5’s leading traditional WAF provides to protect web applications from threats like the OWASP top 10, but also extends security to the users and protects them against fraud.
F5’s AWAF is going to catch a good deal of fraud attempts, but it can’t stop everything. This especially becomes a problem when attackers resort to “copy paste” farms that use humans to manually enter stolen credentials. To stop that kind of fraud you need artificial intelligence (AI) and machine learning (ML) to detect when a real user is not behaving like the actual account holder. This is where F5’s most recent acquisition of Shape Security comes in – F5’s AWAF & SHAPE solution offers a layered approach to application security & fraud protection.
What is Shape Security?
Shape Security was the fastest growing company in Silicon Valley when F5 announced an agreement to acquire it in late 2019.
Touting big hitting customers like Starbucks and most of the airlines – Shape protects 3 out of 4 applications on all smartphones. Shape’s technology is 100% focused on fraud prevention and is to fraud what a WAF is to web application exploits. The big differentiator with Shape is that it’s a managed service that utilizes AI and ML around aggregated user telemetry data, backed by a human SOC. Given Shape’s massive user base and insight into how they login to applications, they have a huge advantage over the competition in identifying and filtering real users from thieves.
F5 & Shape – Everyone needs a good proxy
In order to use the Shape Enterprise Defense cloud solution you’ll need a flexible and fast proxy to route login traffic to Shape’s SOC so they can do their magic. Guess who has the best proxy in the industry? You guessed it… F5. F5’s BIG-IP full proxy makes it easy to route traffic via iRules to Shape. Since you’re already terminating SSL/TLS with your F5 to crack into the HTTPS stream for WAFing, and advanced application delivery, it makes all the sense to access the login data to protect against fraud in that same decryption / re-encryption cycle.
For really large amounts of traffic, and super low latency customers, Shape can also live as a hardware appliance or a virtual machine closest to your apps. Shape had their own mini proxy for this – but it’s nothing compared to the maturity of the F5 BIG-IP.
You can see why it not only made a lot of sense for F5 to acquire Shape, but it also made a lot of sense for Shape to accept F5 as a suitor. It fulfills Shapes need for a high speed flexible proxy that can route traffic to their SOC, and if needed can function inline with some big honking hardware. If I was a betting man, I’d say we’ll see the Shape proxy deprecated in favor of closer integrations into the BIG-IP full proxy platform.
Layering F5 AWAF & Shape Security
A tiered approach protecting your web applications from exploits and denial of services attacks (DoS), while also protecting your user accounts from fraud, is the strongest security you can offer your Internet facing applications today. F5’s BIG-AWAF coupled with Shape give you a layered approach to security that is second to none.
Since the F5 BIG-IP is fronting all traffic, we are able to perform layer 7 TPS and behavioral DoS mitigations before Shape to protect the applications from intelligent and not so intelligent volumetric attacks. We then let Shape take the brunt of the login filtering, and follow up with security policies that are more specific to the application like bot & WAF
Below are two illustrations to help you understand F5’s layered AWAF & Shape approach
for Login Web Traffic — AWAF & Shape:

Is Shape involved for non-login traffic too?
Nope, Shape is solely focused on fraud typically for logins & checkouts. For non-login/non-checkout traffic you’ll leverage the AWAF w/o Shape diversion:
for Non-Login Web Traffic — AWAF-only:
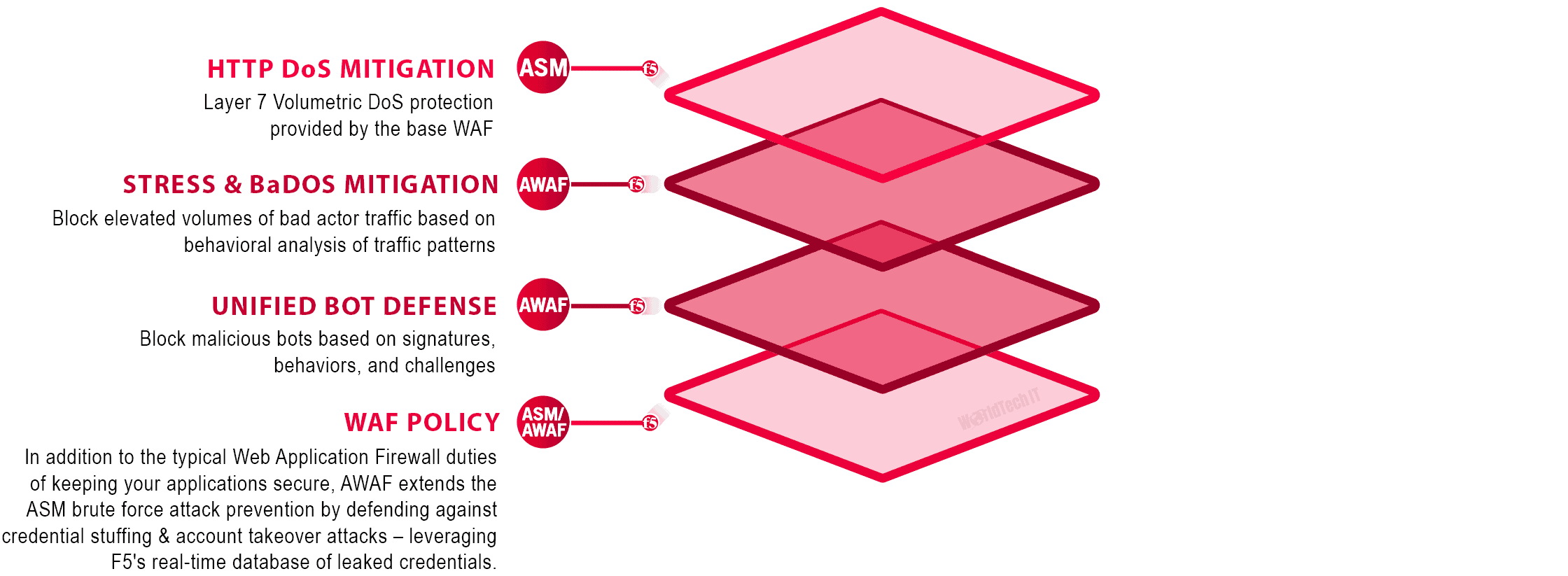
| SECURITY LAYER | PLATFORM | DESCRIPTION |
|---|---|---|
| TPS DOS MITIGATION | F5 ASM | Layer 7 Volumetric DoS protection provided by the base WAF |
| STRESS & BaDOS MITIGATION | F5 AWAF | Block elevated volumes of bad actor traffic based on behavioral analysis of traffic patterns |
| SHAPE DIVERSION | SHAPE SECURITY | Utilizing F5 optimized connection handling we divert the login data to Shape where the traffic runs through behavioral analysis, signature detection, and client fingerprinting. Utilizing data from their aggregated client base in addition to the login data streaming, they’re able to use artificial intelligence to filter out non-human or malicious clients while allowing legitimate clients through – all without using any CAPTCHAs for the best user experience. |
| UNIFIED BOT DEFENSE | F5 AWAF | Block malicious bots based on signatures, behaviors, and challenges |
| WAF POLICY | F5 ASM/AWAF | In addition to the typical Web Application Firewall duties of keeping your applications secure, AWAF extends the ASM brute force attack prevention by defending against credential stuffing & account takeover attacks – leveraging F5’s real-time database of leaked credentials. |
What’s Next for F5 & Shape?
Integration, integration, and integration. We suspect F5 is going to continue to integrate Shape deeper into their stack and products. I mentioned the iRule to route traffic, but I’m sure you’ll be able to turn Shape on as a subscription with a click of a button soon for both BIG-IP and the recently acquired NGINX platform.
Arguably the most aligned integration “today” is F5’s Silverline & Shape integration. Silverline is a managed service by F5 that offers enterprise-grade DDoS prevention and managed Cloud WAF. Adding Shape immediately allows Silverline to offer the same technology behind Shape Enterprise Defense to fight fraud – just at a lower touch, and price point. With Silverline Shape Defense, customers receive updates about once a month, opposed to Shape Enterprise defense, which is a complete white glove service meant for large traffic and or high monetization sites.
Bigger picture, and probably the most interesting, is going to be how F5 integrates Shapes AI & ML technology with the rest of BIG-IP – not only application security, but application delivery as well. Recently F5 has been preaching about “adaptive applications” – ie apps that can shrink, grow, heal, and provide security & auth based on the environment, type of user, and how they’re being utilized at that point in time. Sounds like make-believe right? I don’t think so, if one company has all the pieces to make it happen, it’s F5. I’m very interested to see how their efforts around adaptive apps plays out.
The future is bright for F5 and Shape – I’m excited to see where things go from here as the smart folks from F5, Shape, and NGINX join forces.
WorldTech IT has been integrating Shape’s technology with F5 since Shape’s early days, and we’re experts at developing security policies to layer F5 ASM/AWAF with Shape. You can now purchase Shape Enterprise Defense and Silverline Shape Defense from WorldTech IT and leverage us to assist in implementing our proven layered AWAF & Shape approach. You’ll not only have the best technology, but also the leading experts in the space implementing it.




Leave a Reply